
Across your Entire Digital Perimeter
and your Supply chain
.svg)





Your Vendor Risk Management for compliance fully Automated!
.svg)
.svg)
.svg)
.svg)
.svg)
.svg)
.svg)
.svg)
.svg)
.svg)
.svg)
.svg)

Streamline Vendor Risk Assessments with End-to-End Automation

What You Can Do:

Instantly launch assessments using pre-built or custom AI-generated templates.

Track responses in real time and auto-escalate delays or incomplete submissions.

Trigger next steps: document uploads, approval routing, remediation.
Why It Matters:

Reduce assessment time by up to 80%.

Improve consistency, transparency, and compliance.

Stop manually chasing vendors.


Instantly Identify
Your Riskiest Vendors. Before It’s Too Late
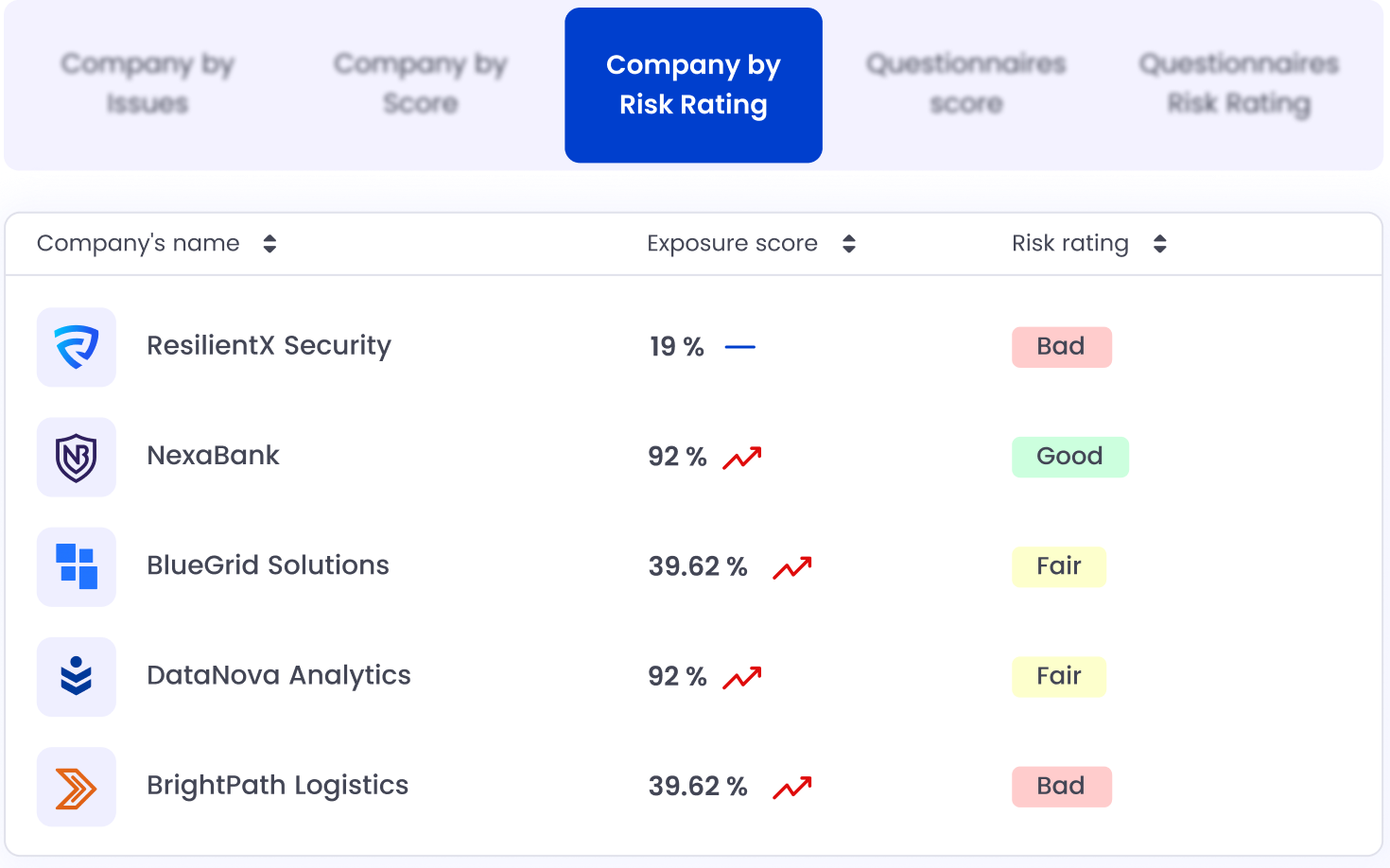
What You Can Do:

Automatically score third parties based on security posture, vulnerabilities, and criticality.

Receive alerts on posture changes or new exposures (CVEs, misconfigurations, leaks).

Prioritize remediation efforts based on potential impact and compliance relevance.
Why It Matters:

Static assessments miss fast-moving threats.

Always know where your biggest risks are.

No need for manual analysis or spreadsheets.
.svg)

Centralize Vendor Risk Across the Entire Lifecycle
.svg)
What You Can Do:

Centralize all vendor data, certifications, and compliance evidence in one secure platform.

Automate workflows to request documents, send reminders, and trigger next steps. No manual follow-ups needed.

Generate audit-ready reports for NIS2, DORA, ISO 27001 and internal governance.
Why It Matters:

Juggling spreadsheets, emails, and folders creates risk.

Gain full control of your vendor ecosystem.

Stay compliant and prepared with smart automation.
.svg)
Strengthen Your Supply Chain Security
Take control of your vendor ecosystem. Identify risks, ensure compliance, and act fast to protect your business.



.svg)

.svg)
.svg)
.svg)

.svg)
.svg)

.svg)
.svg)
.svg)
.svg)
.svg)
.svg)
.svg)


.svg)
.svg)
.svg)
.svg)












