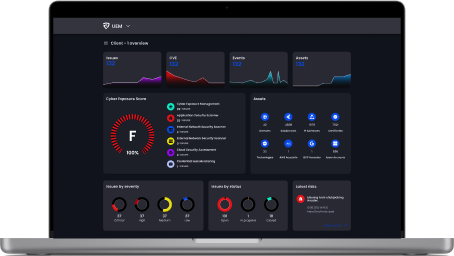
Credential Leak Monitoring
Take proactive approach to ensures the safety and integrity of your sensitive information, enabling prompt action to mitigate potential risks.




Public and Private Leaks
We differentiate between public and private leaks to provide you with a clear understanding of your exposure. Public leaks are often found on readily accessible websites and databases, while private leaks are hidden within more secure, restricted areas. By identifying and categorizing these leaks, we help you prioritize responses based on the severity and potential impact on your organization.

.svg)

Credentials related to Assets not only Emails
Our monitoring goes beyond just email addresses to include a wide range of credentials linked to your organization’s assets. This includes usernames, passwords, API keys, and other sensitive data tied to your systems and applications. By capturing this broader spectrum of information, we ensure a more comprehensive protection of your digital footprint.
Credentials with Context
Understanding the context of leaked credentials is crucial for effective risk management. Our solution provides detailed insights into the circumstances surrounding each leak, including the source, time, potential password in clear text and potential impact.


.svg)
Credential leak Report
Get your credential leaks Comprehensive Report to make informed decisions and strengthen your defenses effortlessly

Ready to see for yourself?
Test drives all platform features for yourself. No commitment and No credit card!



.svg)
.svg)
.svg)
.svg)



.svg)
.svg)
.svg)
.svg)
.svg)
.svg)
.svg)
.svg)

.png)